This article is a part of a series on Address Resolution Protocol (ARP). Use the navigation boxes to view the rest of the articles.
- Traditional ARP
- Proxy ARP
- Gratuitous ARP
- ARP Probe and ARP Announcement
We’ve talked about Traditional ARP, where a node is requesting another node’s MAC address. We’ve also talked about Proxy ARP, where a node is answering an ARP request on behalf of another node. Which brings us to another iteration of ARP known as Gratuitous ARP.
A Gratuitous ARP is an ARP Response that was not prompted by an ARP Request. The Gratuitous ARP is sent as a broadcast, as a way for a node to announce or update its IP to MAC mapping to the entire network.
There are two typical use cases for Gratuitous ARP, and we will look at both of them after looking at the packet structure.
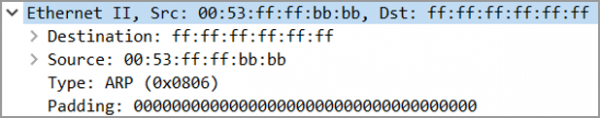
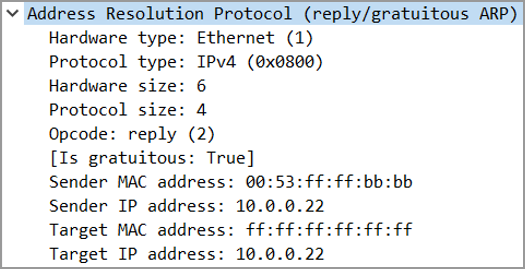
Gratuitous ARP Packet Structure
The main item to point out in the Ethernet header is the Destination MAC. Notice this frame is addressed to
ffff.ffff.ffff, making it a Broadcast frame.
Similarly, in the ARP payload, the Hardware and Protocol type and the Hardware and Protocol Size also serve the same purpose as they did in traditional ARP.
The Opcode is set to
2, indicating a response. Despite the fact that this packet did not actually follow a request.
This is why it is said that a Gratuitous ARP is broadcast ARP Response, that was not prompted by an ARP Request.
The Sender MAC and Sender IP contain the ARP mapping the initiator is advertising. These two are the important part of the ARP Packet. They are the reason the ARP packet exists.
The Target MAC address is
ffff.ffff.ffff – a reflection of the Destination MAC address. But in reality, the contents of this field are irrelevant – they are ignored in a Gratuitous ARP. Some implementations of ARP will use 0000.0000.0000 in this field.
Lastly, the Target IP address once again confirms the IP address that this particular ARP mapping is being created for.
Gratuitous ARP Use Cases
Now that we’ve understood the packet contents of a Gratuitous ARP, we can look at their specific use cases. There are two primary cases we will illustrate for Gratuitous ARP: updating ARP mappings and redundancy.
Updating ARP Mapping
The first use case is pretty straight forward, a node can use a Gratuitous ARP to update the ARP mapping of the other hosts on the network should the node’s IP to MAC mapping change.
This might happen if a user manually modifies their MAC address – they retain the same IP address, but now have a new MAC address. Therefore, the ARP mapping for all the nodes which are communicating with this user must be updated.
That being said, manually changing the MAC address is pretty rare. However, you do sometimes see this in redundant Cloud or Virtual environments, where a particular Virtual Machine (VM) ‘jumps’ to a new physical box – the same VM’s IP address is now being served by a different physical machine.
Redundancy
Much more substantial is Gratuitous ARP’s use case in situations where redundancy or failover between two devices are used.
With redundancy, you typically have two scenarios: two devices sharing an IP address, but each having their own MAC address. Or, two devices sharing both an IP address and a MAC address.
In both of these cases, Gratuitous ARP is critically important to ensure the continued ability to communicate with the IP address as it shifts between the two redundant devices. Below are examples of each scenario and how Gratuitous ARP is employed.
Redundant IP Addresses
In this scenario, only the IP address is redundant. Two devices will share a single IP address, but each device has their own unique MAC addresses.
Our example will use two Routers sharing the IP address
10.0.0.1. The hosts in our example will be using this shared IP address as their default gateway.
When one of the routers experiences a failure, the other router sends a Gratuitous ARP.
The specific contents of the Gratuitous ARP match the packet structure described above, but the essential purpose of the packet is to let everyone on the network know that the IP
10.0.0.1 is now being served by the other router’s MAC address.
Upon receiving the Gratuitous ARP, all the hosts update their ARP tables with the new mapping so they can continue to send traffic to their default gateway IP address through the non-failed Router.
The process continues indefinitely in the case of the opposite router failing. Note, that this particular animation uses routers as the example, but nearly any type of device that shares an IP address with another device will use Gratuitous ARP in this manner.
Redundant IP and MAC Addresses
In this scenario, both the IP address and the MAC address are redundant. Two devices will share both an IP address and a MAC address.
Our example will again use two Routers, but this time they will be sharing the IP address
10.0.0.1 and the MAC address 0053.ffff.1111.
The hosts will still use the shared IP address as their default gateway, but in this example their ARP mapping will never need to change – the shared IP address
10.0.0.1 will always map to the shared MAC address 0053.ffff.1111.
Despite the hosts’ ARP mapping never needing to be updated, Gratuitous ARP is still crucial. But not for the sake of updating the hosts’ARP mapping, but for the sake of updating the switch’s MAC address table so the shared MAC address is associated with the correct port. Recall, switches learn MAC address mappings from the Source MAC address of any received frame.
Notice, as a router fails, the other router sends a Gratuitous ARP. The switch then updates its MAC address table with the new location of the device that owns the shared MAC address.
Again, the specific contents of the Gratuitous ARP match the packet structure described above. But the purpose is for the Switch to learn the new location of the shared MAC address.
In this way, frames sent by the hosts addressed to
0053.ffff.1111 will always egress the correct switch port.
First Hop Redundancy Protocols (FHRPs) like HSRP or VRRP use this exact strategy to enable both routers to share the same IP address and MAC address. Gratuitous ARP is instrumental to enable this type of functionality.
You can download a packet capture of a Gratuitous ARP here. Or, you can download a packet capture of HSRP’s Gratuitous ARPs enacting the last animation of IP and MAC redundancy. Both can be studied using Wireshark.


Comments
Post a Comment
https://gengwg.blogspot.com/