When cloning from a smaller hard drive to a
larger solid state drive, there is potential for system recovery
partitions to prevent the cloning software from properly scaling your C:
drive. If this happens, you’re essentially left with a recovery
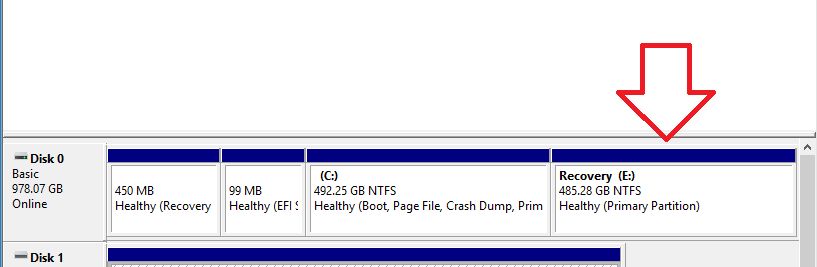
partition that’s eating up a majority of the drive’s space, as the
screenshot in Disk Management below illustrates. Typically, a recovery
partition should only be around 10-15GB. The recovery partition might
not always be visible in Windows® Explorer, so you might need to go into
Disk Management before you can see it.
 Because the
cloning software couldn’t alter the recovery partition during the
cloning process, you can’t go into Disk Management and shrink the
recovery, then expand the C: partition to have a more appropriate size.
The recovery partition will have some sort of security permission
settings, or some service using the partition, which will prevent easy
alteration of the space.
Because the
cloning software couldn’t alter the recovery partition during the
cloning process, you can’t go into Disk Management and shrink the
recovery, then expand the C: partition to have a more appropriate size.
The recovery partition will have some sort of security permission
settings, or some service using the partition, which will prevent easy
alteration of the space.
You have several options to work around this issue. One would be using third-party partition management tools, which can manually adjust the partitions’ sizes to your liking. Some popular options for partition tools are EaseUS™ Partition Master, AOMEI® Partition Assistant, and Paragon® Partition Manager. These tools are not supported by Crucial, so be sure to use online resources for help with the software. Please note that you typically can’t modify partitions on a drive currently running your OS, so creating bootable versions of such software may be required.
An alternative option is to go into Disk Management (Control Panel/Administrator Tools/Computer Management/Storage/Disk Management), and simply try to delete the recovery partition, then right-click your cloned drive and use the Extend Volume option to give the free space back to the OS partition. This is best done when booting from your old drive’s OS, as Disk Management’s resizing options are typically limited when adjusting the drive being booted from. If you delete your recovery partition, you are doing this at your own risk – in some rare situations, the OS can be tied to the recovery partition. As long as you have not erased your old Windows drive, you can use it as a backup in the event that you accidently break windows on the SSD. The recovery partition can be supplemented by creating a recovery disk, or purchasing one from the system manufacturer. If the Delete option is grayed out, you may have better luck putting your old drive back in, booting to it, then trying to delete the recovery on the SSD with it connected as a secondary drive.
Similar space “loss” can occur if your software does not resize partitions, or isn’t configured to do so correctly. This will typically be reflected as a block of “unallocated space” after the C: and recovery partitions.
Lastly, a clean install of the Windows OS will eradicate any factory recovery partitions and create a clean C: drive that utilizes all available space on the disk.

You have several options to work around this issue. One would be using third-party partition management tools, which can manually adjust the partitions’ sizes to your liking. Some popular options for partition tools are EaseUS™ Partition Master, AOMEI® Partition Assistant, and Paragon® Partition Manager. These tools are not supported by Crucial, so be sure to use online resources for help with the software. Please note that you typically can’t modify partitions on a drive currently running your OS, so creating bootable versions of such software may be required.
An alternative option is to go into Disk Management (Control Panel/Administrator Tools/Computer Management/Storage/Disk Management), and simply try to delete the recovery partition, then right-click your cloned drive and use the Extend Volume option to give the free space back to the OS partition. This is best done when booting from your old drive’s OS, as Disk Management’s resizing options are typically limited when adjusting the drive being booted from. If you delete your recovery partition, you are doing this at your own risk – in some rare situations, the OS can be tied to the recovery partition. As long as you have not erased your old Windows drive, you can use it as a backup in the event that you accidently break windows on the SSD. The recovery partition can be supplemented by creating a recovery disk, or purchasing one from the system manufacturer. If the Delete option is grayed out, you may have better luck putting your old drive back in, booting to it, then trying to delete the recovery on the SSD with it connected as a secondary drive.
Similar space “loss” can occur if your software does not resize partitions, or isn’t configured to do so correctly. This will typically be reflected as a block of “unallocated space” after the C: and recovery partitions.
Lastly, a clean install of the Windows OS will eradicate any factory recovery partitions and create a clean C: drive that utilizes all available space on the disk.
Comments
Post a Comment
https://gengwg.blogspot.com/